Zero Trust AI Security
Zero Trust Security for AI
Manage ShadowAI, Control Unauthorized Access, and Enforce AI Guardrails:
Streamlined, Agent-Free Setup in Under 5 Minutes.
Trusted & Advised by leaders across

Lumeus.AI
Zero Trust Security for AI that's
Private and GenAI-Based
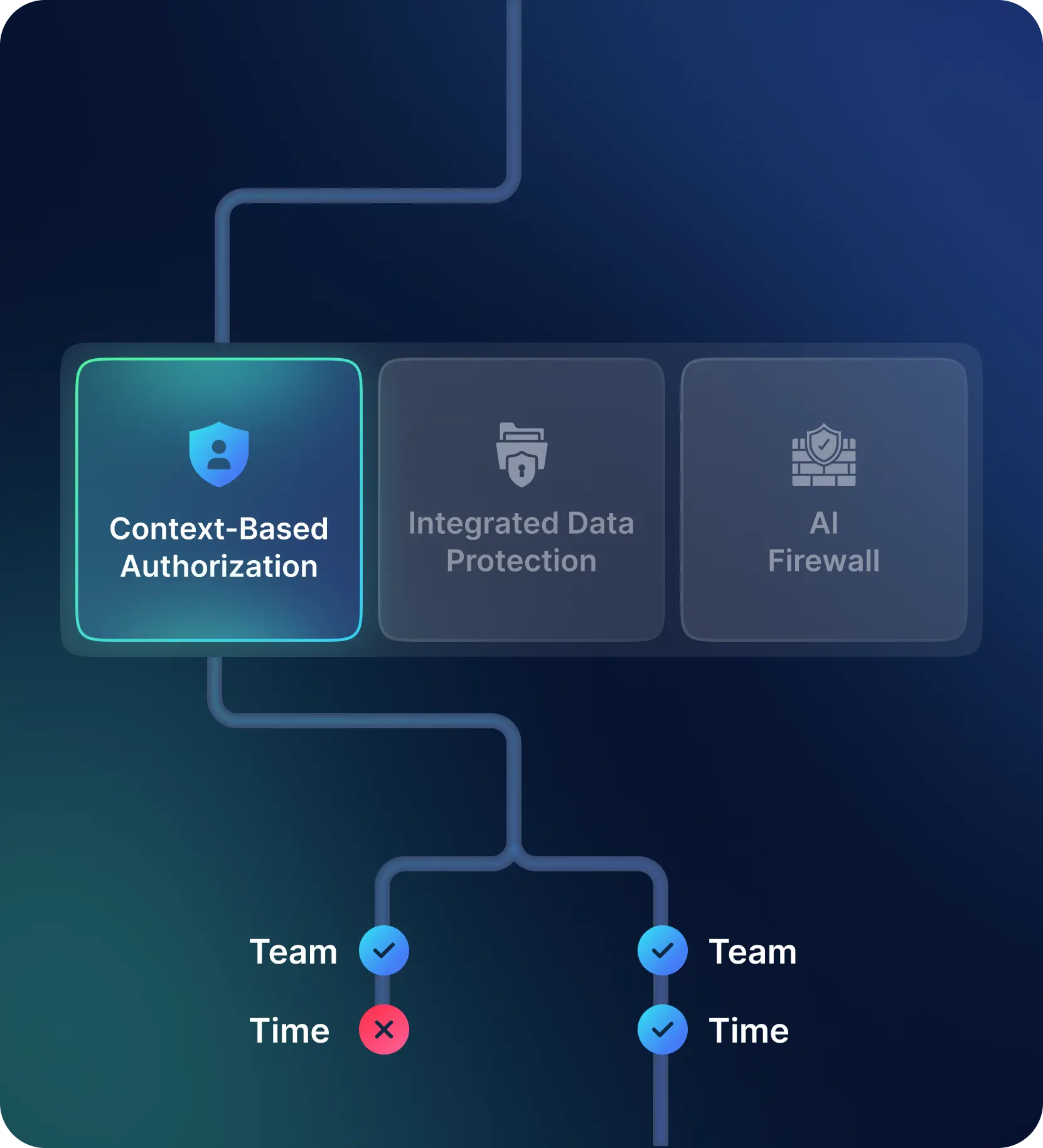
Context-Based Authorization
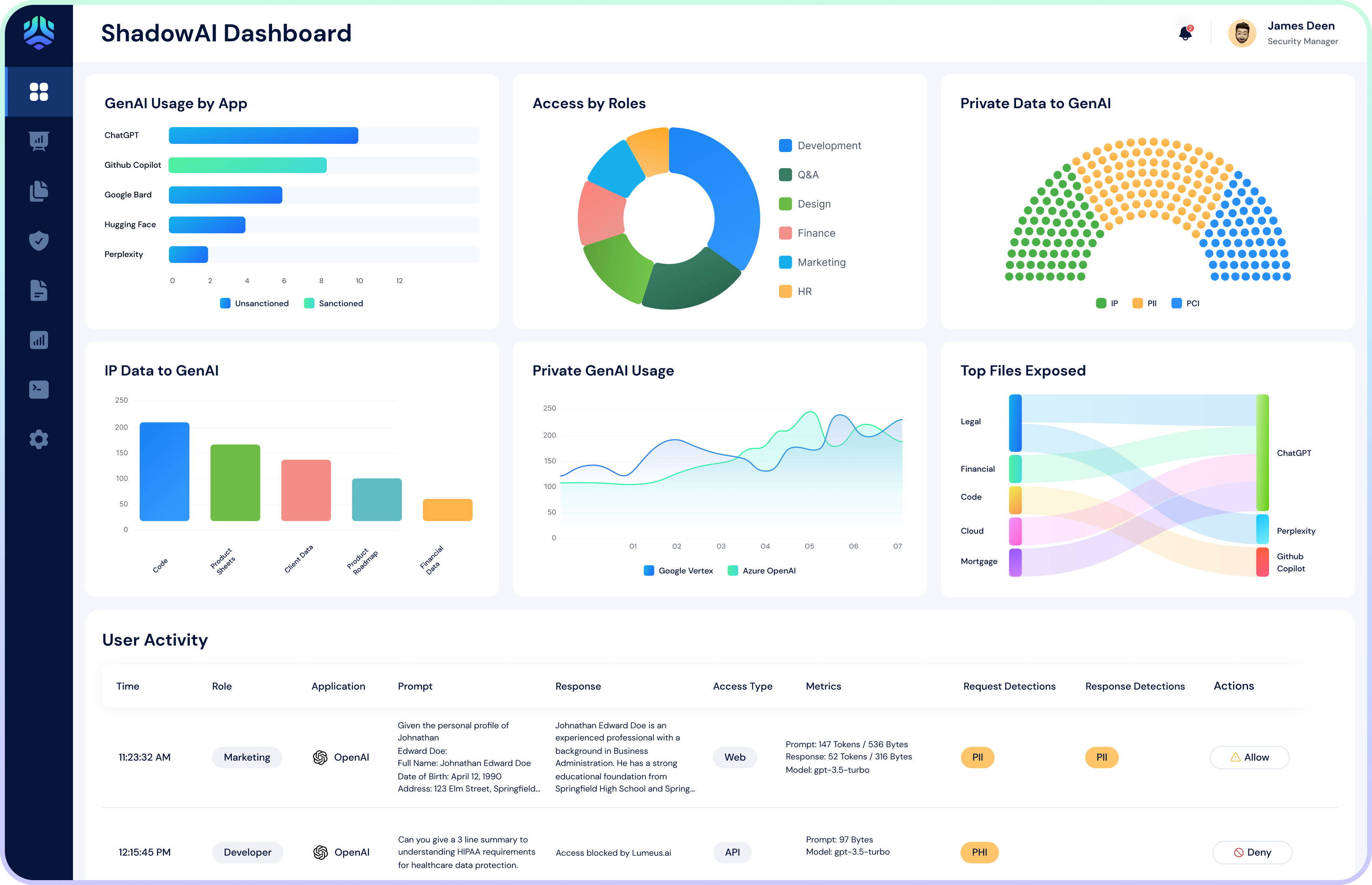
In today’s AI-centric world, secure access is key. Traditional access was role-based, but now we need more. Enter Topic-Based Access Control (TBAC) – it helps prevent AI misuse in sensitive areas like violence or hate.
For private Large Language Models (LLMs), human reviews are common for sketchy content. These need to be permission-based and recorded for compliance.
In short, Secure AI Access should include:
- Role-Based Access for users and apps
- Topic-Based Access to manage AI misuse
- Workflow-Based Access for human reviewers
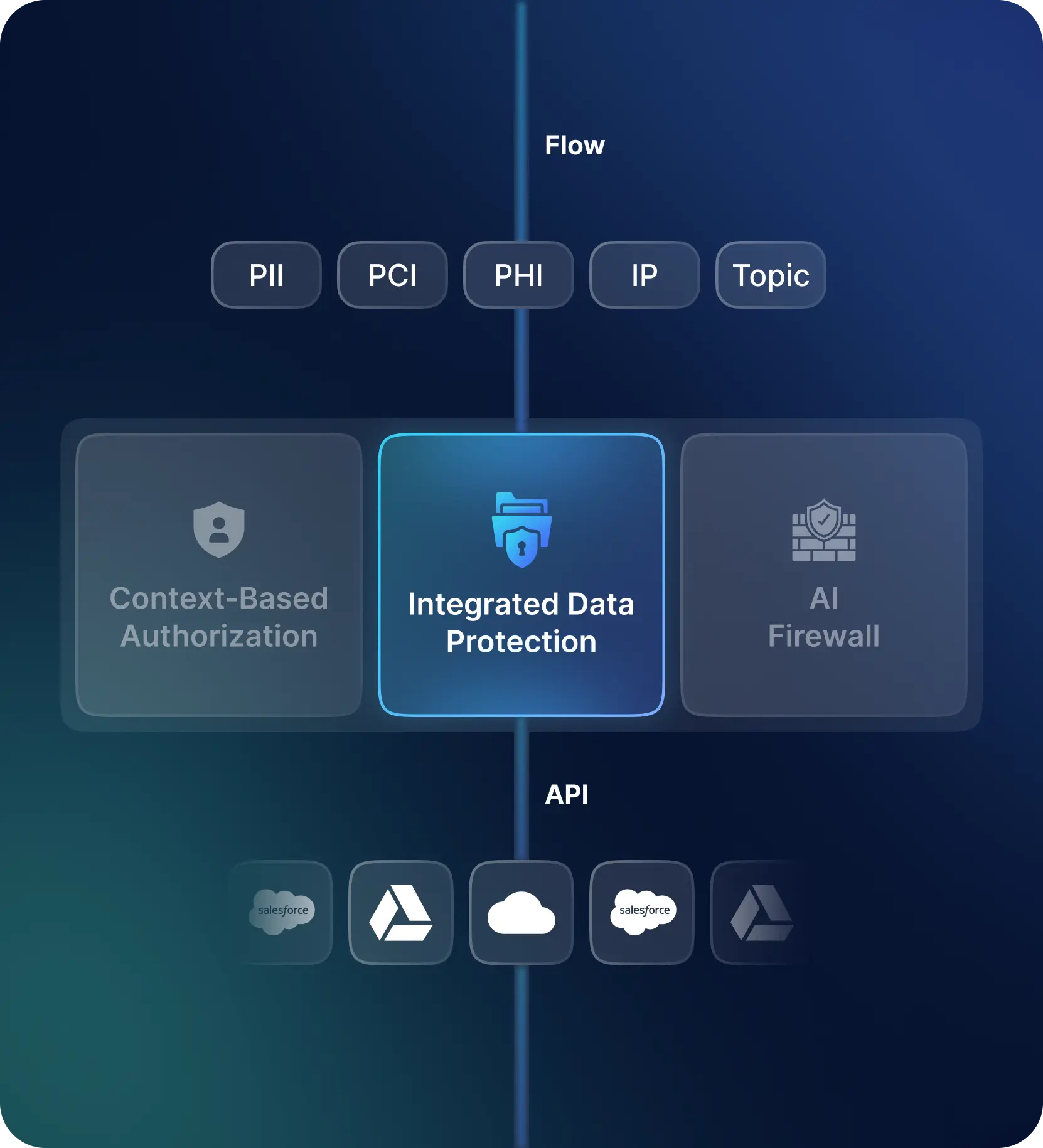
Integrated Data Protection
AI Access in enterprises is similar to Data Access, just with different access methods. For instance, while SQL is used for accessing a PostgresDB, natural language is employed for LLM/AI interactions.
Our focus is on comprehensive Data Protection for:
- Preventing sensitive data leakage from User to AI
- Shielding against exposure of sensitive data from Private LLMs
- Protecting data from poisoning during training or fine-tuning stages
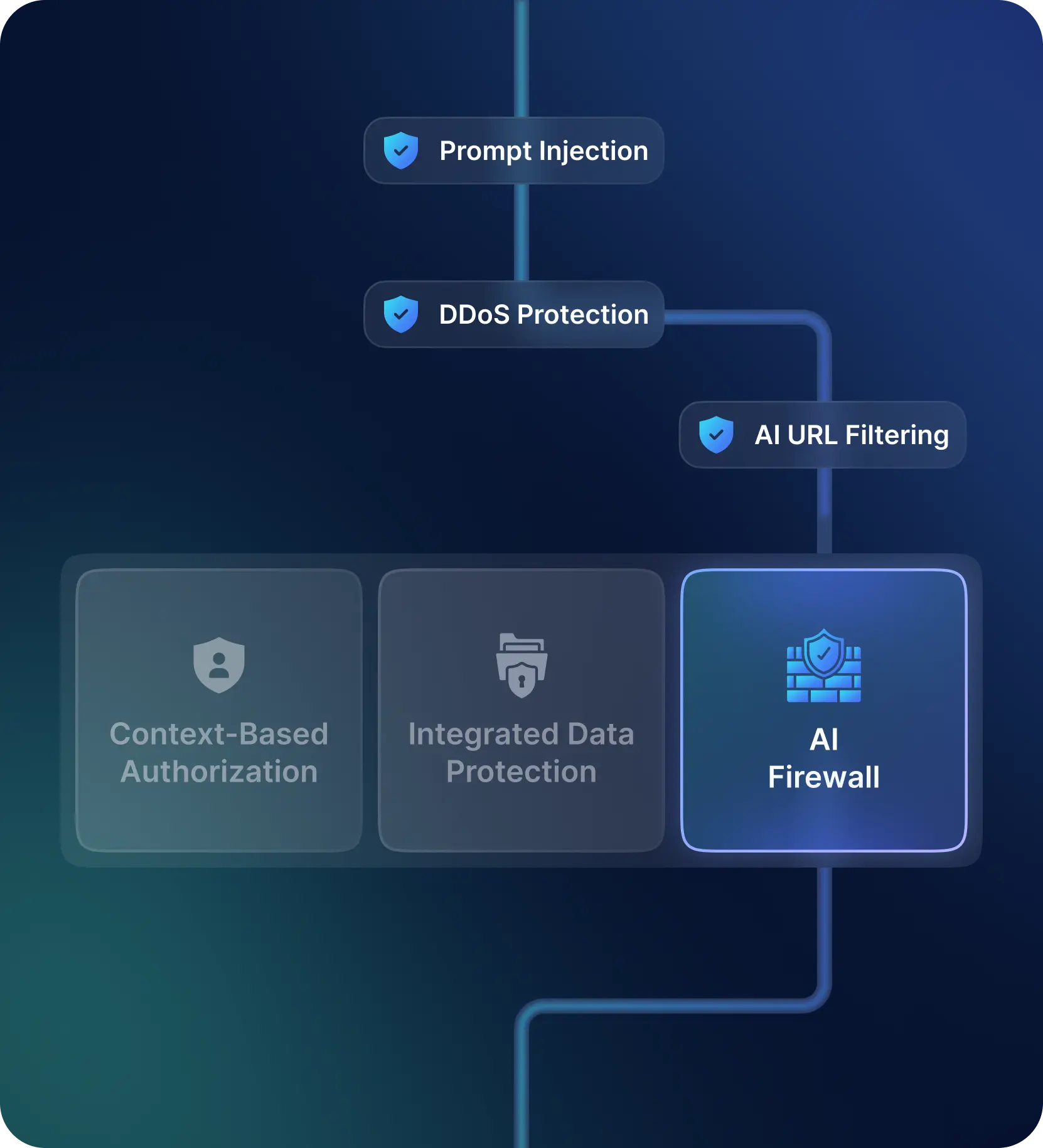
AI Firewall
Next Generation firewalls (NGFW) have long defended against threats from Layer 3 to Layer 7. Now, we’re seeing the emergence of an AI Layer atop the existing application layer. This new layer requires novel controls for both incoming and outgoing traffic, integrated seamlessly with current network security infrastructure. This means no new installations for applications or endpoints.
Key AI Firewall Requirements for safeguarding AI Traffic include:
- Defending against Prompt Injection Attacks
- Mitigating Supply Chain Risks
- Preventing Model Denial of Service Attacks
Integrations
Product Integrations

The Lumeus Difference

ShadowAI Visibility
Our solution is hassle-free, bypassing the need for browser plugins or endpoint apps with existing VPN/ZTNA. It integrates effortlessly. You gain immediate control and insight into AI and data traffic, on day one.

Network- Based
We enhance your existing network security from vendors like Palo Alto, Fortinet, ZScaler and others adding a layer that specifically manages AI and data traffic. This means more visibility & control by integrating seamlessly.

Unified AI+Data Security
We combine secure data access, AI user access, and AI app security into one straightforward product. This unified approach is efficient, especially as AI evolves as an intelligent data store with unique interactions